How to Protect Your Business from Cyber Attacks: A Guide for End Users

Introduction:
In today’s digital world, cybersecurity is a critical component for businesses of all sizes. Cyber attacks can be devastating, leading to data breaches, financial losses, and reputational damage. In this guide, we’ll explore the importance of cybersecurity in business and provide practical advice on how to protect your business from cyber attacks.
Understanding Cyber Attacks:
To protect your business from cyber attacks, it’s important to understand what they are and how they occur. Cyber attacks refer to malicious attempts to damage, disrupt, or gain unauthorized access to computer systems, networks, or devices.
There are several types of cyber attacks, including:
- Phishing attacks
- Malware
- Ransomware
- Social engineering attacks, and
- Password attacks
Cybercriminals use various methods to launch these attacks, such as email phishing, social media scams, and software vulnerabilities.
Common Cybersecurity Threats for Businesses:
- Phishing attacks are one of the most common cybersecurity threats faced by businesses. They typically involve an email that appears to be from a legitimate source, such as a bank or vendor, asking the recipient to provide personal information or click on a link.
- Malware, another common threat, refers to software that is designed to damage or disrupt computer systems.
- Ransomware is a type of malware that encrypts a victim’s files, making them inaccessible until a ransom is paid.
- Social engineering attacks involve tricking people into providing sensitive information or performing actions that compromise security.
- Password attacks refer to attempts to guess or steal passwords.
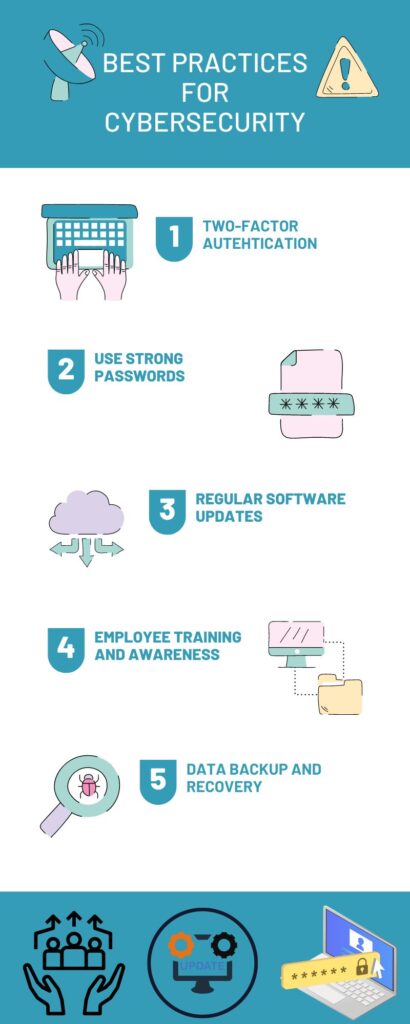
Best Practices for Cybersecurity:
Implementing best practices for cybersecurity can help protect your business from cyber attacks.
- Strong passwords, for example, can make it harder for cybercriminals to gain unauthorized access to your systems.
- Two-factor authentication provides an additional layer of security by requiring a second form of authentication, such as a code sent to a mobile device.
- Regular software updates can also help prevent cyber attacks by patching vulnerabilities.
- Employee training and awareness is crucial for preventing social engineering attacks, as employees need to be able to identify and avoid phishing emails and other scams.
- Data backup and recovery can help mitigate the impact of a cyber attack by allowing you to restore data that has been lost or corrupted.
Protecting Your Business from Cyber Attacks:
Protecting your business from cyber attacks involves a multi-layered approach. Conducting a security audit can help identify vulnerabilities and areas where security can be improved. Creating a cybersecurity policy can provide guidelines and procedures for employees to follow, and can help ensure that everyone in the organization is on the same page when it comes to cybersecurity. Using security software and tools, such as firewalls and antivirus software, can help detect and prevent cyber attacks. Implementing access controls can limit access to sensitive information and systems, reducing the risk of unauthorized access. Monitoring and responding to threats is also important, as cyber attacks can occur at any time.
Conclusion:
In summary, protecting your business from cyber attacks is essential in today’s digital age. Understanding the types of cyber attacks and how they occur is the first step in developing a comprehensive cybersecurity strategy. Implementing best practices such as strong passwords, two-factor authentication, and employee training can help prevent cyber attacks. Conducting a security audit, creating a cybersecurity policy, using security software and tools, implementing access controls, and monitoring and responding to threats are all important components of a comprehensive cybersecurity strategy. By taking these steps, you can help ensure that your business is protected from cyber attacks and minimize the risk of data breaches, financial losses, and reputational damage.